How to Spot a Phishing Email (3 Easy Clues!)
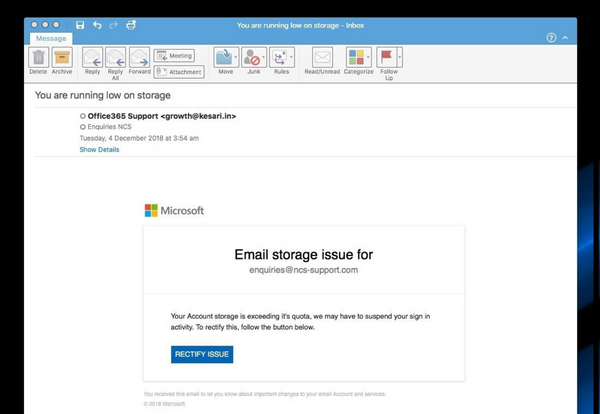
This is an example of the phishing emails we see every day. It is a real email that was sent to one of our generic email addresses.
We have highlighted below some of the clues that show it isn’t an email from who it claims. It is trying to tempt us to a webpage where it can steal our personal information eg user name, password or similar.
In this case, the email claims to be from Microsoft, telling the recipient that their email storage is nearly full:
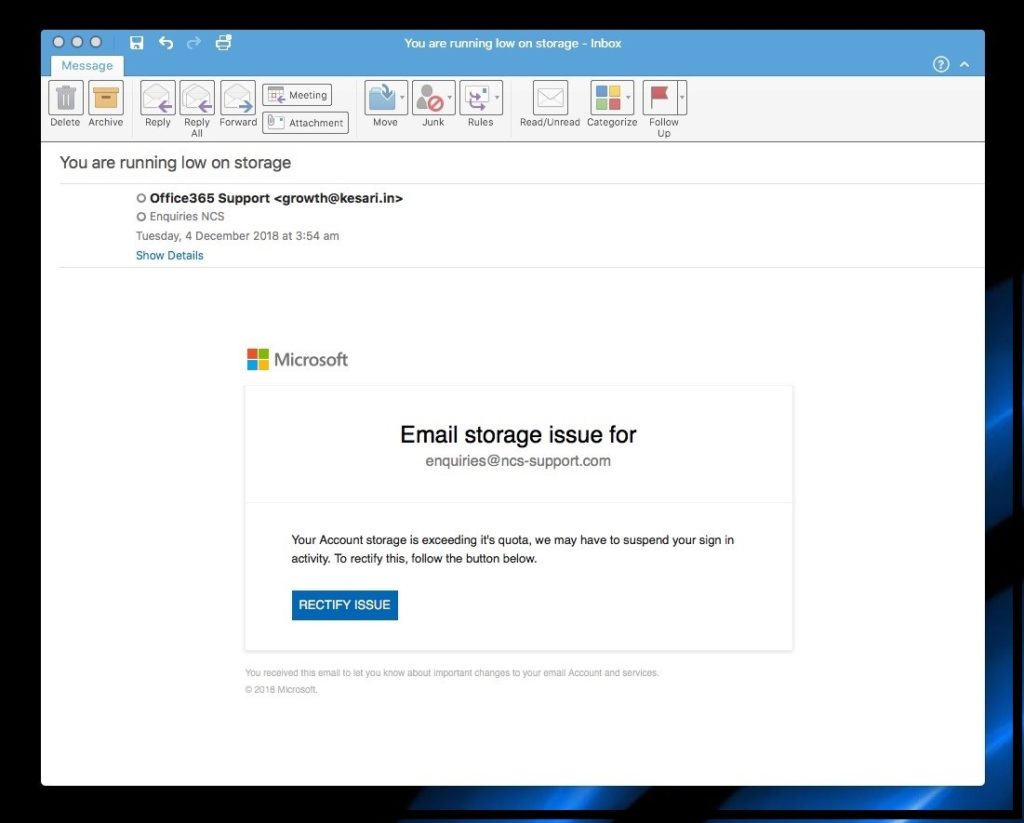
Let’s look at who sent it to us. This is our first clue:
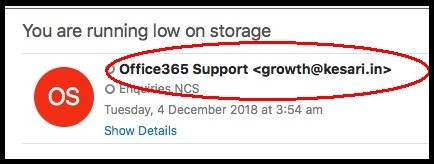
Our email program, Outlook, has been helpful here in displaying the sender’s email address and it is clear right away this email is not from Microsoft. I have never heard of growth@kesari.in before, but I am now alerted to the fact that this email is not a genuine warning from Microsoft.
In real life, you should delete this email at this point and move on with life, but we’ll take our investigation a little further and see what else we find.
Our next clue comes in the body of the message. Look out for random capitalisation of words. Look at the poor grammar and stilted, unnatural-sounding English. These are red flags. Companies like Microsoft, who this is supposed to have come from, employ thousands of people and English is usually a primary language of communication for them. It’s not likely they would send out something with this many mistakes:
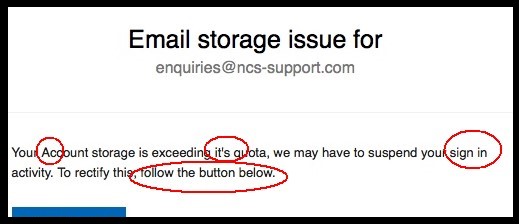
There’s another point to consider here which is relevancy. Have you even got an Office 365 email account? If not, why would they be emailing you? If you do have an Office 365 email account, is it running out of storage space? Have you had a warning message when you last logged in? If not, be suspicious of an email like this that says there’s an issue you weren’t aware of.
Our final clue arrives when we put the mouse pointer over that tempting button that says “Rectify Issue”. This is the “call-to-action” button. It promises to solve the problem for us. Surely it will take us to a website where we’ll be able to resolve this email storage problem we weren’t aware of (hint: it won’t!)
If we hover the mouse over the “Rectify Issue” button – don’t click it, just move the pointer over the button and leave it there – then within a second or two, we’ll get a popup box that shows us where the button links to:
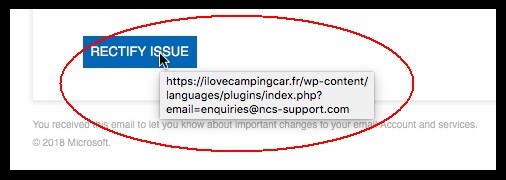
Now you can see this button is not going to take us to a Microsoft website. It’s going to take us instead to a page on a different site called ilovecampingcar.fr.
So, if we click the button it will take us to a site that’s pretending to be Microsoft’s. You can be sure it’s going to ask there for our Office 365 username and password so it can resolve the made-up “email storage issue”.
Purely in the name of research, we clicked the button for you and here’s what happened next. Clicking the button took us to this webpage:
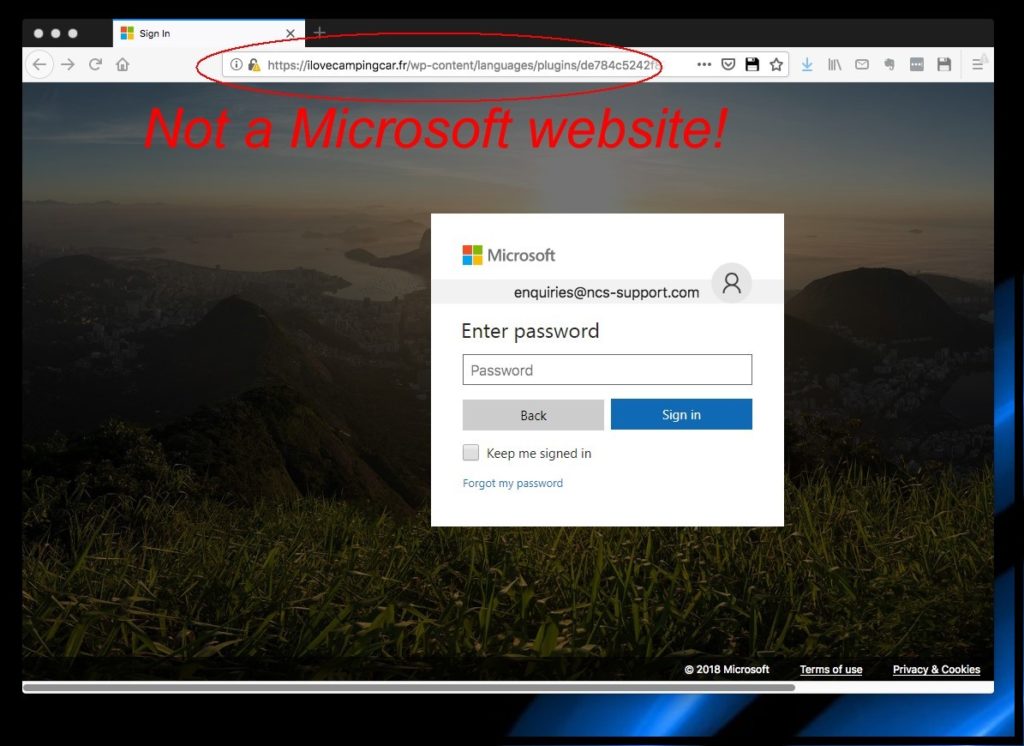
As you can see, this convincing but fake Microsoft login screen has even pre-populated our email address (how thoughtful!) and now all it wants is our password. Obviously, we’re not going to do that.
Note: We have done this on an isolated PC to show how easily people can steal your personal information. Please don’t try this yourself. Also, please keep in mind it is trivial to mess with the code behind the popup web-address box and the email sender’s name at the top of the message so they show you false information. The lesson is not to rely on just one clue, look at the email overall.
Summary
Here are the clues in this particular phishing email:
- The fake sender
- The poorly-written message and the relevancy test
- The call-to-action button or web link (“rectify issue”, “click here to resolve this” etc) that takes us to a webpage that asks for our personal details.
Ultimately, there’s only piece of advice we can give you. If you follow this, it will serve you well:
If you’re not expecting the email, don’t click on any links in it and don’t open any attachments. If in doubt, delete the email.
Posted in News